An Introduction to Multi-Factor Authentication
MFA Knowledgebase (requires login)
How-to install the Microsoft Authenticator app on a Smartphone/Tablet (requires login)
What is Multi-Factor Authentication?
Multi-Factor Authentication (MFA) is a technology we use increasingly often in our daily lives. For example, when you access your online banking application you may be required to respond to a text message sent to your smart phone. The text message communicates a code that you need to input into the banking website. This text message is called a “second factor” and is part of Multi-Factor Authentication – essentially a second way to prove you are who you say you are.
Like the example above, MFA will allow UGDSB employees to use multiple “factors” when accessing the board’s Microsoft Azure cloud services (e.g. Microsoft O365 services, Google services, MS Teams, Outlook Online, OneDrive and other board wide services).
For a simple overview of MFA, you can view this short YouTube video.
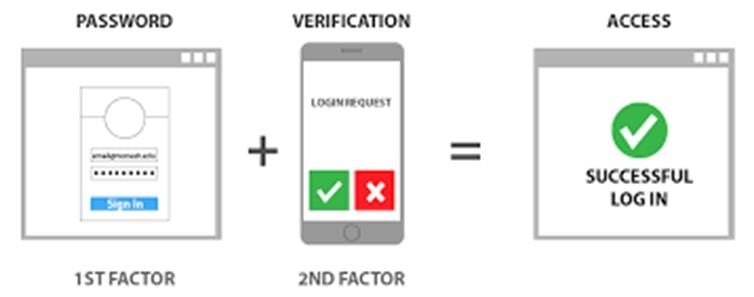
What are MFA Factors?
The first factor is “What You Know” – this is your UGDSB username and password
The second factor is “What You Have” – this is your smartphone with MS Authenticator app installed, a call back number or a physical token.
Why should I use MFA?
MFA is now mandatory for all UGDSB staff.
Using MFA will help mitigate many of the cybersecurity threats the UGDSB faces every day. MFA will also help mitigate potential damage from phishing emails, credential-stealing and malware attempts against the Azure cloud service.
How will MFA affect me?
At this time, the sign-in process for MFA will only apply to UGDSB employees when they access Microsoft, Google and other board applications. Once you have registered for MFA, you will be asked periodically to verify your login when accessing these services. A message will be sent to your smart phone, phone number or physical token to which you need to respond with “Approve” or “Deny”, or with a six-digit code.
UGDSB employees should see a reduction in MFA prompts as the system understands who and where you login. It typically takes 90 days for the requests to noticeably subside.
What are my MFA options?
There are several options to choose from as your second factor for MFA. It is recommended that users have more than one method to help prevent getting locked out:
The Microsoft Authenticator app is the recommended method because of its ease of use and enhanced security. The app can be installed on any smartphone/tablet and can be configured to use either a push notification or a verification code. Please note, if you currently have a board provided smartphone, you are required to use the Microsoft Authenticator app.
SMS text messages can be used to send a 6-digit code to your mobile phone number. Phone Calls can be made to a mobile phone number (do not use a home number or school extension.
A board-provided OTP hardware Token that provides a 6-digit code every minute (this can easily be attached to a set of keys).
What is the recommended verification method for MFA?
The Microsoft Authenticator mobile app is the recommended method for most users. It takes up very little space and provides both online and offline code options to log in. It is an application you control and install and if other accounts, such as for Google, Facebook, or GitHub, you can add them to the Microsoft Authenticator app for two-step verification. The Authenticator app works with any app that uses two-step verification and any account that supports the Time-based One-time Password (TOTP) standards.
Add non-Microsoft accounts to the Microsoft Authenticator app
What I do not consent to using my personal smartphone?
No worries! If you are not comfortable using your personal smartphone for Multi-Factor Authentication, you are more than welcome to choose to use a board-provided OTP hardware token.
Do I need to carry my smartphone or OTP hardware token with me every day?
Yes, you will. The system is set to require MFA based on certain conditions making the request unpredictable for users.
When will MFA roll out start?
The IT Department will be rolling out MFA for Microsoft Azure cloud services and applications to all staff/educators, on July 1, 2022.
How do I get MFA support?
Technical support for MFA is available during normal business hours Monday through Friday from 8:30 a.m. to 4:30 p.m. If you need support, please call (519) 822-4420 ext. 247 or submit a ticket online at UG Support.
